How to Prevent “Man in the Middle Attacks”
There are different types of security exploits like
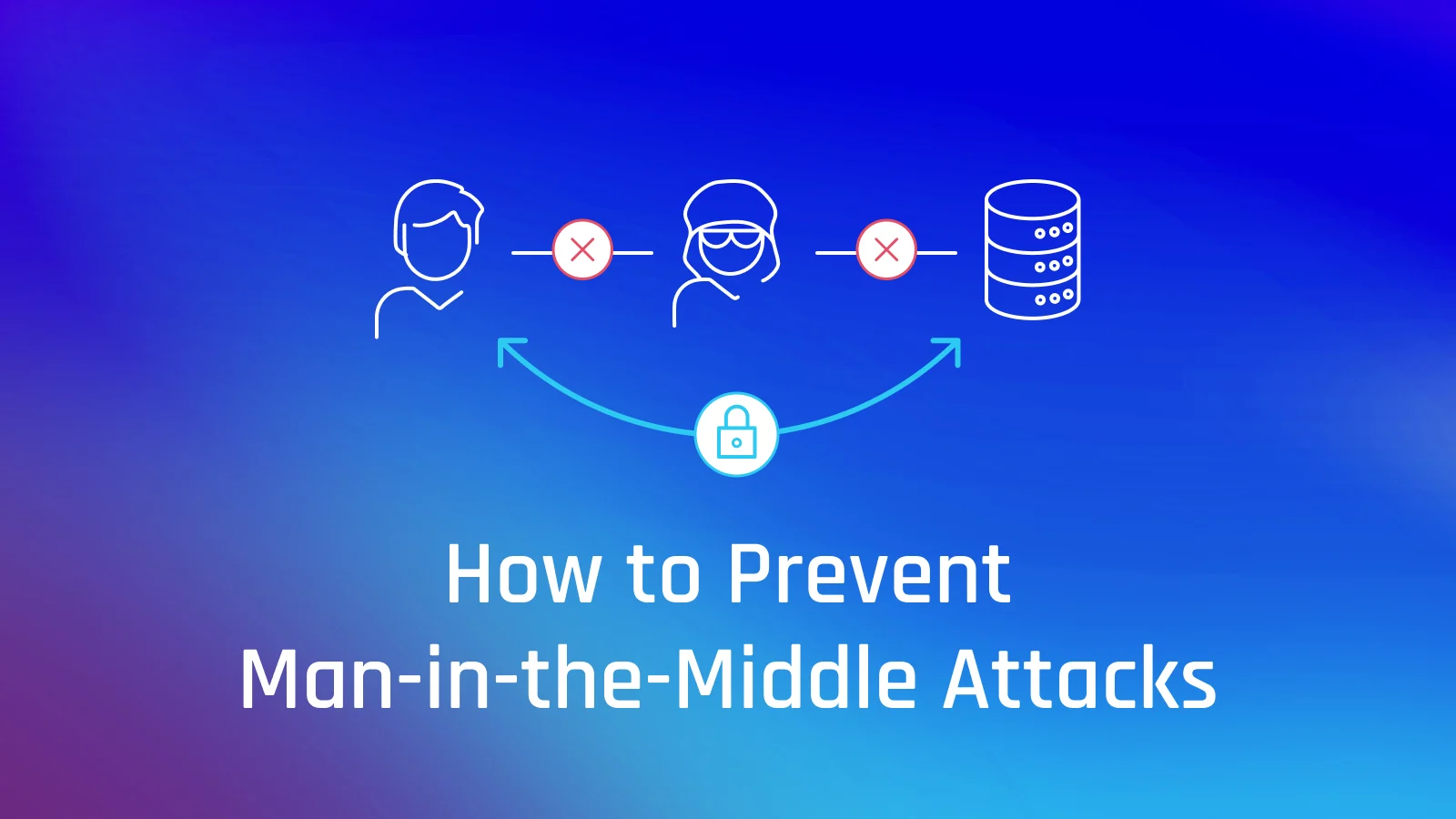
“Man in the Middle Attack” is an eavesdropping cyberattack in which an attack secretly intercepts and relays messages between two communicating parties. The attacker inserts themselves into the middle of the communication channel and pretends to be a legitimate participant.
The two entities communicating cannot identify man-in-the-middle, and they suppose that their communication is safe.
The man-in-the-middle makes independent connection, relays, control, and possibly change the communication between the directly communicating parties. Also, the man-in-the-middle can capture and control sensitive information.
Types of Man-in-the-Middle Attacks
There are multiple varieties of man-in-the-middle attacks. Here are some that should be on your radar:
- Internet Protocol (IP) spoofing: The attacker changes the source IP address of a website, server, or device for masking purposes.
- Domain Name System (DNS) spoofing: The hacker changes the domain names of the websites to redirect and reroute traffic through fake websites.
- HTTP spoofing: Attackers redirect a browser session to an unsecured website.
- Secure Sockets Layer (SSL) Hijacking: The hacker uses a separate computer or webserver to intercept the information.
- Email Hijacking: The attacker gains control of email accounts to control transactions. The hacker might send a fake bank email address to spoof the user’s email account.
- Wi-Fi Eavesdropping: The attacker uses fake or malicious Wi-Fi to route traffic through their desired server.
- Session Hijacking: The man-in-the-middle steals browser cookies to steal personal data and passwords.
- Cache Poisoning: The attack poisons ARP (Address Resolution Protocol) to reroute traffic to a malicious network.
How to prevent man-in-the-middle attacks
It is essential to prevent man-in-the-middle attacks. Preventing these attacks stops someone from accessing our internet connection remotely.
How to protect against man-in-the-middle attacks is a high-rated question for users, as these attacks can result in substantial financial losses. The hackers intercept high-value communication to steal sensitive information like credentials and passwords.
It’s important to protect your communication and stop man-in-the-middle attacks. Here are some steps to prevent them:
Use Standardized Protocols for safe Communication.
Always used standardized protocols like SSH (Secure Socket Shell), Google’s QUIC (Quick UDP Internet Connection), and TLS (Transport Layer Security) protocols as they provide encryption and other data protection tools.
These protocols harden Transmission Control Protocol (TCP) that requires clients and serves to exchange security and trust certificates verified by an independent third party called a Certificate Authority (CA). These certificates authenticate the messages if the original key fails to authenticate due to a man-in-the-middle attack. The sessions end if the client’s or server’s ID is not verified or declared invalid.
Strong WEP/WAP Encryption on Access Points
The wireless access points must have a robust encryption mechanism to prevent man-in-the-middle attacks. Weak encryption allows cyberattacks to include brute force into the network.
HTTP Public Key Pinning (HPKP)
HPKP or certificate pinning also provides security for preventing man-in-the-middle attacks. It includes a list of pinned public key hashes during the first transactions. For the following transactions, the server must provide one or more keys to authenticate the transactions.
Public Key Pair-Based Authentication
Public key pair-based authentication is another secure method to prevent man-in-the-middle attacks. Public key pair-based authentication methods can be implemented at different network stack layers. Unlike other authentication methods, it uses two separate keys for encryption and decryption, which makes it impossible for hackers to spoof the network. Most internet protocols like SSH implement this method for providing secure communication.
Always Use Secure Connections
A secure connection is always the first defense against man-in-the-middle attacks, as secure connections protect communication. The users must avoid connecting to weak-security internet connections and public Wi-Fi as they may contain security vulnerabilities.
The hacker spoofs the devices to connect illegally and steal your information. The user should connect with secure websites and servers as fake websites, or insecure websites can also help hackers to spoof your communication.
To avoid this, only make connections that you know are secure and use the latest protocols.
Avoid Phishing Emails
The hackers use phishing emails to send malicious links that help them to control your communication. The received email will look like an original email bank from a known source. However, attackers use resembling names, email addresses, and similar email structures. The user clicks on the malicious link that connects the user with the hacker’s setup, unwittingly subjecting themselves to a man-in-the-middle attack.
Use Virtual Private Network (VPN) Encryption
VPNs are a good idea for encrypting internet connections and data, as hackers cannot decrypt data without the secret encryption key. VPN provides secure communication even if hackers have hacked the internet connection. VPNs also work perfectly with insecure internet connections and public Wi-Fi, as attackers cannot extract encrypted data easily.
Use Strong Router Login Credentials
It is important to set strong router login credentials to make it difficult for users to connect to the internet. Most people forget to change the default login credentials of the routers, making it easier for cybercriminals to hack and infect routers. The hacker can access all communication if an attacker gains access to a router. Make sure you change the router password to something secure!
Force Connections to use HTTPS
HTTPS is HTTP with encryption and security, providing secure communication using a public-private key exchange. It prevents man-in-the-middle attacks as the hacker cannot sniff. Therefore, the strict use of HTTPS offers secure communication between servers and users.
Conclusion
The man-in-the-middle attack is a cybersecurity threat in which a hacker intercepts the communication between two users or a user and server. The hacker relay on communication and registers himself as a legitimate person. The user may not be able to identify man-in-the-middle attacks. Different methods prevent man-in-the-middle attacks, like using standardized protocols, strong WEP/WAP Encryption on Access Points, secure connections, VPN encryption, strong router login credentials, and HTTPS.
Fully decentralized

End to end encryption
Full randomization








